This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Reference
More than 30 IDM realisations in the Czech Republic and abroad
Identity Management
ČEZ
Implementation of central identity and role management in CEZ Group. More than 10 types of systems are connected to SUN Identity Manager (7.1), and more than 40,000 accounts, and more than 100,000 roles are managed.
Project goal
The main goal of the Identity Management integration project was to ensure unified and centralized management of user accounts and roles on individual systems used in the CEZ Group and managed by CEZ ICT Services. This goal was fulfilled by implementing the Sun Java System Identity Manager application, which manages the connected end systems (SAP, MS Active Directory, Oracle Portal, and others) and keeps all user accounts consistent and in line with authoritative data sources (SAP HR, External User Database).
Another goal of the project was to provide role management, a role request process using the Service Desk application with role selection from the registry, approval of role assignments by a matrix of approvers, and auditability of all changes.
The final objective of the project was to simplify the work of end users and implement single sign-on to selected applications. Thus, after logging into Microsoft Active Directory, the user is automatically logged into other systems in which they have an account.
Project description
The project was implemented and managed by specialists from AMI Praha a.s. and ČEZ ICT Services, a. s. Partner Sun Microsystems supplied the project know-how and an experienced IT architect ensured the implementation. Avnet and Profinit contributed to the development of some functionalities. A significant part of the development in the area of identity and role registries was provided by ČEZ ICT Services, a.s.
Benefits for the customer
- Automatic actions and controls to increase security
- Unified process for managing user accounts and roles
- Auditability of changes and requests
- Uniform password policy
- Single sign-on across systems
- Simplify work for Service Desk operators
- Uniform user data across all systems
Solution description
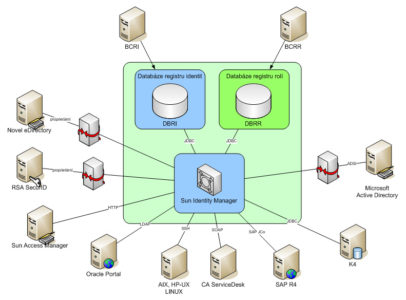
After a thorough analysis, a centralized solution and implementation of Sun Java System Identity Manager was proposed, which retrieves data from the authoritative SAP HR system (via the SAP XI interface) and further propagates (or processes and propagates) it to other connected systems. Standard adapters (SAP, Oracle Portal, RSA SecurID, Novell NDS, etc.) were used to connect the systems, where some functionalities were implemented in J2EE, and Scripted JDBC adapters (AIX, RedHat, Passport), where all functionalities were completely programmed. Some systems (MS AD, Novell NDS, RSA) require a Sun Gateway that is installed on the connected system and mediates communication between the Identity Manager and the end system. Identity Manager creates a single database of virtual accounts for all employees with a single set of attributes assigned to them. These accounts are then paired with and managed by the accounts on each endpoint system. The creation, update, and termination of user accounts on individual end systems is thus secured by a single application (Identity Manager) and a single management process. This process is characterized by various approval workflows that are defined in Identity Manager. All processes are then audited and reportable.
At the customer’s request, the functionality for requesting, assigning, and managing roles and permissions has been implemented in Identity Manager. Roles are managed in the BCRR application (an application developed internally by the customer), from where Identity Manager retrieves them and assigns them to individual users. Application roles (assigns certain permissions), login roles (assigns access to the system), and business roles (bundles several roles according to business requirements) are used. These roles can be requested by the respective employee as well as his/her supervisor across all connected systems. A role property can be time-limited and can also carry a license. A mandatory part of the role definition is an approvers matrix. The process of role assignment is conditional on its approval, according to the workflow at several levels (e.g., license, methodologist, supervisor, system administrator). All approvals take place directly in the Identity Manager application, and both role assignment and approval are audited and transmitted to the ServiceDesk application, where the request is initiated and tracked.
The project has implemented a central password policy and history that centrally monitors the strength and validity of passwords, enforces password changes, and sends information to users. Here, great emphasis was placed on the quality encryption of passwords during their transfer and storage.
Due to a large number of passwords and security standards, the project also addressed the issue of Single Sign-On. Primarily it was about IdM itself using Access Manager from Sun Microsystems, for SAP, SAP Portal and Oracle Portal systems Kerberos tickets were used. For Identity Manager, 2 login policies were chosen – for the user interface, single-factor authentication was used, which is done by verifying the name and password in MS Active Directory and uses single sign-on (SSO). For the administration interface, two-factor authentication was used, which is done by verifying the name from the RSA SecurID system and the so-called passcode, followed by the password from Microsoft Active Directory.
